Linux Kernel Can Be Exploited Remotely; Kernel Prior To 5.0.8 Affected
W e keep coming across various security loopholes in different software on a daily basis, but it rarely happens that Linux kernel gets crippled by a high-impact flaw. However, things are looking a bit different today as millions of Linux systems have been found to be affected by a massive flaw.
It’s being reported that the kernel versions prior to 5.0.8 are affected by a race condition vulnerability. For those who aren’t aware, race condition attacks take place when a system designed to perform tasks in a particular sequence is made to perform two or more operations simultaneously. During this state, interference could be caused by a trusted/untrusted process.
In the case of Linux kernels prior to 5.0.8, the race condition flaw was discovered in rds_tcp_kill_sock in net/rds/tcp.c. “There is a race condition leading to a use-after-free, related to net namespace cleanup,” mentions the CVE description of the flaw.
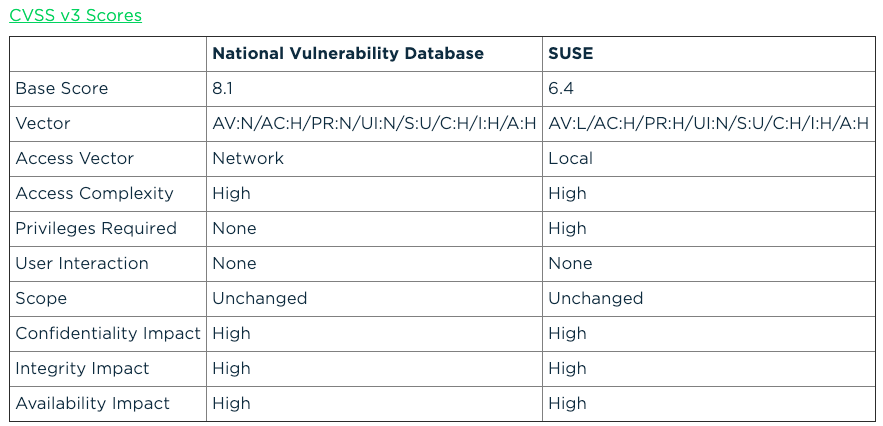
It’s worth noting that on the NIST database, this CVE-2019-11815 vulnerability is listed with a high impact score of 5.9. However, as this flaw is difficult to exploit, it’s been given a low exploitability score of 2.2; the overall base score is 8.1.
For further information, you can also refer to the security advisories from different Linux distributions: Debian , Red Hat , SUSE , Ubuntu .
As per Bleeping Computer , hackers can launch attacks on Linux machines using specially created TCP packets to execute arbitrary code.
It’s worth noting that the flaw has already been fixed during late-March with the release of Linux kernel 5.0.8. So, you’re advised to update your kernel as soon as possible and install the patch.
Also Read: How To Upgrade Linux Kernel In Ubuntu And Linux Mint Easily With Ukuu